Hello,
I would like to present results of my research on (most likely) latest ACCDFISA 2.0 ransomware outbreak. Various info found on several forums led to conclusion that it's not possible to obtain decryption key for that ransomware. Someone stated that paid the ransom, and got two encryption keys for his files. At this moment, it's entirely possible to generate 2nd decryption key by mine tool.
Ransomware is quite complex and I didn't spent too much time on it's reverse analysis, however general flow looks like this:
1. Attack vector is ussually opened RDP ports, patient I got had bruteforced password
2. Ransomware is being installed as "WinSamSS" service, pointing to lsassw86s.exe file, so it will work and encrypt your files all the time - unlikely other ransomware, which justs quietly deinstalls.
3. During first startup, when no configuration files are inside ProgramData, it generates 1st password and ID basing on VolumeSerialId and other stuff. 1st password looks like F771703112FAC4FF3082B05BCF1B70EAC6E0FT33518nAj9-EJ808+3bF0Fr3x1)2bFn3^Fd3IFXF71S484lDwCU7T9663A(BB4A4X6b3k7V7F2p0L (actual dump from debug session)
4. Encryption key is being sent to IP 85.93.5.18
5. Encryption (by cmd-line rar, after encryption freespace wiped by sdelete) is started using 1st password, once done or breaken, apporiate files is created in ProgramData and System32 (SysWow64) to mark finish of 1st phase
6. Afterwards, txt file with 1st password in ProgramData is being erased, and now ransomware switchs to 2nd phase which uses 2nd encryption key only
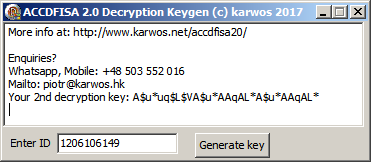
7. 2nd encryption key is much simpler, and don't use any pseudorandom artifacts (unlike 1st pass - which use ADVAPI32 Crypto* funcs). It uses just ID, which you can find in each filename, and do some simple math on it. So yeah, I reversed it and written Application to generate that 2nd key.
Just wanna say, that i've readen on many forums that it's surely not possible to decrypt files encrypted by that ransomware. Yeah, it's true if you look at 1st password, however it's worth to try because lot of your files might be encrypted by 2nd key in 2nd phase. I have no idea what success rate will It have in real-life, however I am pretty sure vast amount of ppls will find it usable in scenarios like reboot during 1st encryption, connection of some pendrive / external HDD storage to infected PC after 1st phase finish, probably others... Just grab it and try.
Download link - click here
Seems file is detected by 2/40 AVs as a false positive, confirmation here. I will ask MS to rework that, about Sophos - seems they triggered false-positive just because of "keygen" in file content... Weird.
Last update:
1. According to webpage visit-stats, ransomware attacking almost always in weekends (friday-saturday), most views I see on mondays! Curious.
2. There is some small posibilty to reconstruct stack frames and maybe extract 1st key (accdfisa20 didn't cleanup stack memory), so if you are after FRESH infection, don't restart your PC - dump yoyour memory contents, it increases your chances. In some cases, hiberfil.sys and pagefil.sys could be helpfull aswell.
If you have found this software usefull, and decrypted some files, or would like to support futher work on counter-ransomware projects, feel free to donate developer:
Author:
Piotr Karwowski " karwos "
Mailto: piotr (at) karwos.hk
Whatsapp, Mobile: +48 503552016
Keywords:
ACCDFISA 2.0 2017
(!! to get password email id to bracode17@gmail.com !!)
sdelete
lsass86vl.exe
wblsys32vt86exkdll.dll
lsassw86s.exe
sdelete.dll
default2.sfx
decryptaesfiles.htm
33454657978078423464562234678456468
rar encrypted
sfx encrypted
WinSamSS service
accdfisa2
accdfisa
Update:
13.06.2017, 11:50 CET

